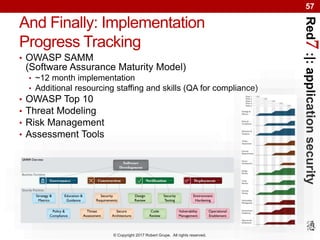
The document introduces the Secure Software Development Life Cycle (SSDLC) for web and mobile applications, emphasizing the importance of security in the software development process to mitigate risks such as data breaches. It discusses common vulnerabilities, costs associated with poor security practices, and regulatory compliance requirements while advocating for proactive measures to protect applications throughout development. The SSDLC integrates security measures from the start, leading to reduced risk and enhanced compliance with regulatory obligations.