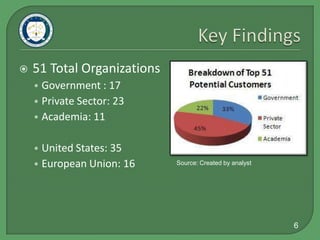
This document summarizes GreyLogic's market research on cyber intelligence customers, competitors, and best practices. It identifies the top 12 potential government and private sector customers in the US and EU. 16 competitors were identified, with the closest being iDefense Labs, iSIGHT Partners, and SecureWorks. The best markets are large US government agencies and companies relying on IT. Within the EU, the UK and countries vulnerable to Russian influence are best. Government and private sector each make up around half of the potential customers. Industry best practices include strategic alliances, online community building, and gradual pricing structures.