AI, Blockchain, IoT GDPR Compliance AT A Glance
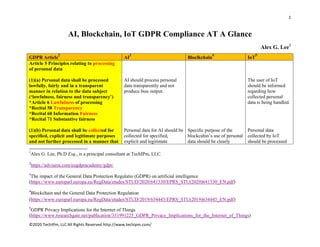
- 1. 1 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ AI, Blockchain, IoT GDPR Compliance AT A Glance Alex G. Lee1 GDPR Article 2 AI 3 Bloclkchain 4 IoT 5 Article 5 Principles relating to processing of personal data (1)(a) Personal data shall be processed lawfully, fairly and in a transparent manner in relation to the data subject (‘lawfulness, fairness and transparency’) *Article 6 Lawfulness of processing *Recital 58 Transparency *Recital 60 Information Fairness *Recital 71 Substantive fairness (1)(b) Personal data shall be collected for specified, explicit and legitimate purposes and not further processed in a manner that AI should process personal data transparently and not produce bias output. Personal data for AI should be collected for specified, explicit and legitimate Specific purpose of the blockcahin’s use of personal data should be clearly The user of IoT should be informed regarding how collected personal data is being handled. Personal data collected by IoT should be processed 1 Alex G. Lee, Ph.D Esq., is a principal consultant at TechIPm, LLC. 2 https://advisera.com/eugdpracademy/gdpr/ 3 The impact of the General Data Protection Regulatio (GDPR) on artificial intelligence (https://www.europarl.europa.eu/RegData/etudes/STUD/2020/641530/EPRS_STU(2020)641530_EN.pdf) 4 Blockchain and the General Data Protection Regulation (https://www.europarl.europa.eu/RegData/etudes/STUD/2019/634445/EPRS_STU(2019)634445_EN.pdf) 5 GDPR Privacy Implications for the Internet of Things (https://www.researchgate.net/publication/331991225_GDPR_Privacy_Implications_for_the_Internet_of_Things)
- 2. 2 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes shall, in accordance with Article 89(1), not be considered to be incompatible with the initial purposes (‘purpose limitation’) Article 13 Information to be provided where personal data are collected from the data subject Article 89(1) Safeguards and derogations relating to processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes (1)(c) Personal data shall be adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed (‘data minimization’) *Recital 78 Organizational Measure for Data Protection *Recital 162 Processing for Statistical Purposes purposes and processed for those purposes. Specific purpose of the AI’s use of personal data should be determined before data collection or training or deployment. A new AI’s use purpose of personal data should be compatible with the original purpose. AI's use of additional personal data should provide a benefit that outweighs any potential risk by including additional personal data. The personal data processed for statistical purpose should not be used for adopting decisions on individuals by AI. communicated to the data subject that they are using blockcahin technology and explained related implications such as that the processing is not limited to the original transaction but that their personal data will continue to be processed thereafter. in relation to the purposes for which those data are collected. Personal data collected by IoT should be limited to what is necessary in relation to the purposes (applications or services to operate) for which they are processed. Article 22 Automated individual decision- making, including profiling *Article 13(2)(f) Information to be provided *Article 14(2)(g) Information to be provided
- 3. 3 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ *Article 15(1)(h) Right of access *Article 21 Right to object (1) The data subject shall have the right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning him or her or similarly significantly affects him or her *Article 4(4) Profiling *Article 6(1) Lawfulness of processing *Recital 71 Substantive fairness (2)(a)Paragraph 1 shall not apply if the decision is necessary for entering into, or performance of, a contract between the data subject and a data controller (2)(b)Paragraph 1 shall not apply if the decision is authorized by Union or Member State law to which the controller is subject and which also lays down suitable measures to safeguard the data subject’s rights and freedoms and legitimate interests (2)(b)Paragraph 1 shall not apply if the decision is based on the data subject’s explicit consent *Article 4(11) Consent (3) In the cases referred to in points (a) and (c) of paragraph 2, the data controller shall implement suitable measures to safeguard Implement some level of human involvement in the decision process (decision supporting tool for final human decision). If possible, use anonymized data. Potential measures are (a) Use pseudonymized data (b) Input Automated decision-making by blockchain smart contracts should be analyzed for compatibility. This is the case particularly for AI algorithms deployed in conjunction with IoT.
- 4. 4 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ the data subject’s rights and freedoms and legitimate interests, at least the right to obtain human intervention on the part of the controller, to express his or her point of view and to contest the decision (4) Decisions referred to in paragraph 2 shall not be based on special categories of personal data referred to in Article 9(1), unless point (a) or (g) of Article 9(2) applies and suitable measures to safeguard the data subject’s rights and freedoms and legitimate interests are in place. *Article 9 Processing of special categories of personal data Article 32 Security of processing (1) Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of processing as well as the risk of varying likelihood and severity for the rights and freedoms of natural persons, the controller and the processor shall implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk, including inter alia as appropriate: the pseudonymization and encryption of personal data; data related to the data subject and other parameters used by AI algorithm for automated decision can be provided upon request. A careful consideration should be given for processing sensitive personal data (personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, trade union membership, genetic state, biometric signal, health status, sex life or sexual orientation).
- 5. 5 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ (a) the ability to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services; (b) the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident; (c) a process for regularly testing, assessing and evaluating the effectiveness of technical and organizational measures for ensuring the security of the processing. Article 16 Right to rectification The data subject shall have the right to obtain from the controller without undue delay the rectification of inaccurate personal data concerning him or her. Taking into account the purposes of the processing, the data subject shall have the right to have incomplete personal data completed, including by means of providing a supplementary statement. *Article 29 Working Party Article 17 – Right to erasure (‘right to be forgotten’) Trained AI algorithm can be used for transfer learning because the data that are Rectifying data on private blockchains can be possible through a change of the relevant transaction record by re-hashing subsequent blocks where this is facilitated by the respective technical and governance set-up. Rectifying data on public blockchains may be possible by means of providing a supplementary statement to make incomplete data complete. Blockahin should provide at least means for blocking access to the data (e.g., IoT should be designed from the start to meet suitable detailed requirements of personal data rectification, erasure, portability, and transfer.
- 6. 6 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ The data subject shall have the right to obtain from the controller the erasure of personal data concerning him or her without undue delay and the controller shall have the obligation to erase personal data without undue delay … *Article 19 Notification obligation regarding rectification or erasure of personal data or restriction of processing Article 20 Right to data portability The data subject shall have the right to receive the personal data concerning him or her, which he or she has provided to a controller, in a structured, commonly used and machine-readable format and have the right to transmit those data to another controller without hindrance from the controller to which the personal data have been provided … Article 45 Transfers on the basis of an adequacy decision A transfer of personal data to a third country or an international organization may take place where the Commission has decided that the third country, a territory or one or more specified sectors within that embedded in trained AI algorithm are no longer persona data. Data analysis using AI is likely to involve cross-border transfer and multiple parties. destruction of the private key, which would have the effect of making data encrypted with a public key inaccessible). If possible, use anonymized data (e.g., non-reversible encryption of data, Zero- knowledge proofs). There may be some cases that interoperability among various blockchain solutions cab be an issue. Blockchain should allow data subjects to obtain information about where their data has been transferred to in line with the informational duties applying to third country transfers. Transfer of personal data to multiple devices located in many locations including in other Nations is likely in the IoT
- 7. 7 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ third country, or the international organization in question ensures an adequate level of protection. Such a transfer shall not require any specific authorization. *Article 46 Transfers subject to appropriate safeguards *Article 47 Binding corporate rules Article 24 Responsibility of the controller *Article 4(7) ‘controller’ means the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data; where the purposes and means of such processing are determined by Union or Member State law, the controller or the specific criteria for its nomination may be provided for by Union or Member State law. *Article 5(2) The controller shall be responsible for, and be able to demonstrate compliance with, paragraph 1 (‘accountability’). *Article 26 Joint controllers Two or more controllers jointly determine the purposes and means of processing. *Article 28 Processor *Article 29 Processing under the authority of the controller or processor (1) Taking into account the nature, scope, context and purposes of processing as well In AI applications, the measures include controls To identify the actors determining the purposes and means of data processing in a specific use case ((joint- )controllership), it is not only necessary to consider the specificities of that use case and the manner in which personal data is handled, but moreover to carefully examine the governance design of a given blockchain.
- 8. 8 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ as the risks of varying likelihood and severity for the rights and freedoms of natural persons, the controller shall implement appropriate technical and organizational measures to ensure and to be able to demonstrate that processing is performed in accordance with this Regulation. Those measures shall be reviewed and updated where necessary. (2) Where proportionate in relation to processing activities, the measures referred to in paragraph 1 shall include the implementation of appropriate data protection policies by the controller. (3) Adherence to approved codes of conduct as referred to in Article 40 or approved certification mechanisms as referred to in Article 42 may be used as an element by which to demonstrate compliance with the obligations of the controller. Article 25 Data protection by design and by default *Recital 28 Introduction of Pseudonymisation (1) Taking into account the state of the art, the cost of implementation and the nature, scope, context and purposes of processing as well as the risks of varying likelihood over the adequacy and completeness of training sets, over reasonableness of the inferences, over the existence of causes of bias and unfairness. With regard to AI, these measures should include controls over the representativeness of training sets, over the reasonableness of the inferences and over the absence of unfairness and discrimination. Appropriate security Whoever uses blockchain technology, should ensure that the technical specificities are such to enable compliance with the GDPR. The data controllers are obliged to make sure that the processes of blockchain governance to Special design consideration in GDPR-compliance IoT system should be given considering automatic communication without human intervention between
- 9. 9 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ and severity for rights and freedoms of natural persons posed by the processing, the controller shall, both at the time of the determination of the means for processing and at the time of the processing itself, implement appropriate technical and organizational measures, such as pseudonymzation, which are designed to implement data-protection principles, such as data minimization, in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects. (2) The controller shall implement appropriate technical and organizational measures for ensuring that, by default, only personal data which are necessary for each specific purpose of the processing are processed. That obligation applies to the amount of personal data collected, the extent of their processing, the period of their storage and their accessibility. In particular, such measures shall ensure that by default personal data are not made accessible without the individual’s intervention to an indefinite number of natural persons. (3) An approved certification mechanism pursuant to Article 42 may be used as an element to demonstrate compliance with measures, such as encryption or pseudonymization, should also prevent ensure that compliance with the GDPR is possible. IoT objects and between IoT objects and persons.
- 10. 10 ©2020 TechIPm, LLC All Rights Reserved http://www.techipm.com/ the requirements set out in paragraphs 1 and 2 of this Article. *Article 42 Certification Article 35 Data protection impact assessment *Article 36 Prior consultation *Article 9 Processing of special categories of personal data *Article 5(1)(e) Storing personal data *Article 40 Codes of conduct *Article 6 Lawfulness of processing (1) Where a type of processing in particular using new technologies, and taking into account the nature, scope, context and purposes of the processing, is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall, prior to the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data. A single assessment may address a set of similar processing operations that present similar high risks. The impact assessment is important in the development of data-protection compliant AI. It would be helpful if regulatory guidance on blockchains to specify whether the use of blockchains creates a high risk to fundamental rights, or whether risk ought to be assessed on a case-by-case basis. IoT data controllers should consider the impact of the personal data processing. Double shield for cybersecurity via AI +blockchain integration may provide data- protection compliant IoT.
