More Related Content
Similar to Cobit 5 for Information Security
Similar to Cobit 5 for Information Security (20)
Cobit 5 for Information Security
- 1. for Information
Security
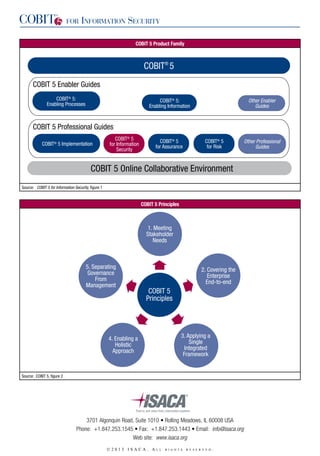
COBIT 5 Product Family
COBIT® 5
COBIT 5 Enabler Guides
COBIT® 5:
Enabling Processes
COBIT® 5:
Enabling Information
Other Enabler
Guides
COBIT 5 Professional Guides
COBIT® 5 Implementation
COBIT® 5
for Information
Security
COBIT® 5
for Assurance
COBIT® 5
for Risk
COBIT 5 Online Collaborative Environment
Source: COBIT 5 for Information Security, figure 1
COBIT 5 Principles
1. Meeting
Stakeholder
Needs
5. Separating
Governance
From
Management
2. Covering the
Enterprise
End-to-end
COBIT 5
Principles
3. Applying a
Single
Integrated
Framework
4. Enabling a
Holistic
Approach
Source: COBIT 5, figure 2
3701 Algonquin Road, Suite 1010 • Rolling Meadows, IL 60008 USA
Phone: +1.847.253.1545 • Fax: +1.847.253.1443 • Email: info@isaca.org
Web site: www.isaca.org
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
Other Professional
Guides
- 2. for Information
Security
COBIT 5 Goals Cascade Overview
Stakeholder Drivers
(Environment, Technology Evolution, …)
Influence
Stakeholder Needs
Benefits
Realisation
Risk
Optimisation
Resource
Optimisation
Cascade to
Enterprise Goals
Cascade to
IT-related Goals
Cascade to
Enabler Goals
Source: COBIT 5, figure 4
Selected Guidance From the COBIT 5 Family
These charts and figures are elements of COBIT 5 and its supporting guides. This excerpt is available as a complimentary
PDF (www.isaca.org/cobit) and for purchase in hard copy (www.isaca.org/bookstore). It provides an overview of the
COBIT 5 guidance, its five principles and seven enablers. We encourage you to share this document with your enterprise
leaders, team members, clients and/or consultants.
COBIT enables enterprises to maximize the value and minimize the risk related to information, which has become the
currency of the 21st century. COBIT 5 is a comprehensive framework of globally accepted principles, practices, analytical
tools and models that can help any enterprise effectively address critical business issues related to the governance and
management of information and technology. Additional information is available at www.isaca.org/cobit.
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
- 3. for Information
Security
Governance and Management in COBIT 5
Governance Objective: Value Creation
Benefits
Realisation
Risk
Optimisation
Resource
Optimisation
Governance
Enablers
Governance
Scope
Roles, Activities and Relationships
Source: COBIT 5, figure 8
Key Roles, Activities and Relationships
Roles, Activities and Relationships
Delegate
Owners and
Stakeholders
Accountable
Instruct and
Align
Set Direction
Governing
Body
Management
Monitor
Report
Source: COBIT 5, figure 9
COBIT 5 Governance and Management Key Areas
Business Needs
Governance
Evaluate
Direct
Monitor
Management Feedback
Management
Plan
(APO)
Build
(BAI)
Run
(DSS)
Monitor
(MEA)
Source: COBIT 5, figure 15
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
Operations
and
Execution
- 4. for Information
Security
Information Security Skills/Competencies
Skills/Competencies
Information security governance
Information security strategy formulation
Information risk management
Information security architecture development
Information security operations
Information assessment and testing and compliance
Source: COBIT 5 for Information Security, Figure 20
Example Stakeholders for Information Security-related Information (Small/Medium Enterprise)
A
Chief executive officer (CEO)
U
A
U
I
U
U
U
Policies
Information Security Dashboard
I
Information Risk Profile
Information Security Review Reports
U
Information Security Requirements
I
Information Security Plan
U
Stakeholder
Information Security Budget
Board
Information Security Strategy
Awareness Material
Information Security Service Catalogue
Information Type
Internal: Enterprise
Chief financial officer (CFO)
A
U
Chief information security officer (CISO)
O
U
O
O
A
A
A
A
U
U
Information security steering committee (ISSC)
A
O
A
U
U
I
U
I
U
U
Business process owner
U
O
U
U
U
Head of human resources (HR)
U
U
U
O
O
O
U
Internal: IT
Chief information officer (CIO)/IT manager
U
O
U
U
U
U
I
Information security manager (ISM)
U
U
U
O
U
O
O
External
Investors
I
Insurers
I
I
I
I
Business Partners
I
I
Vendors/Suppliers
I
Regulators
I
External Auditors
I
I
An indication of the nature of the relationship of the stakeholder for each information type:
A—Approver
O—Originator
I—Informed of information type
U—User of information type
Source: COBIT 5 for Information Security, Figure 17
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
I
I
I
I
- 5. for Information
Security
Advantages and Disadvantages of Potential Paths for Information Security Reporting
Role
Advantages
Disadvantages
Chief executive officer (CEO)
Information risk is elevated to the highest level in
the enterprise.
Information risk needs to be presented in a format that
is understandable to the CEO. Given the multitude of
responsibilities of the CEO, information risk might be
monitored and managed at too high a level of abstraction
or might not be fully understood in its relevant details.
Chief information officer (CIO)
Information security issues and solutions can be aligned
with all IT initiatives.
Information risk may not be addressed due to other
IT initiatives and deadlines taking precedence over
information security. There is a potential conflict of
interest. The work performed by information security
professionals may be IT-focussed and not information
security-focussed. In other words, there may be an
insufficient business focus.
Chief financial officer (CFO)
Information security issues can be addressed from a
financial business impact point of view.
Information risk may not be addressed due to financial
initiatives and deadlines taking precedence over
information security. There is a potential conflict
of interest.
Chief risk officer (CRO)
Information risk is elevated to a position that can also look
at risk from strategic, financial, operational, reputational
and compliance perspectives.
This role does not exist in most enterprises. It is most
often found in financial service organisations. In
enterprises in which a CRO is not present, organisational
risk decisions may be decided by the CEO or board
of directors.
Chief technology officer (CTO)
Information security can be partnered and included in
future technology road maps.
Information risk may not be addressed due to technology
directions taking precedence over information security.
Chief operating officer (COO)
Information security issues and solutions can be
addressed from the standpoint of impact to the business’
operations.
Information risk may not be addressed due to operational
initiatives and deadlines taking precedence over
information security.
Board of directors
(indirect report)
Information risk is elevated to the highest level in
the enterprise.
Information risk needs to be presented in a format that
is understandable to board members, and hence may
become too high-level to be relevant.
Source: COBIT 5 for Information Security, Figure 14
Policy Framework
Policy Framework
Input
Information Security Principles
Mandatory
Information
Security Standards,
Frameworks
and Models
Information Security Policy
Specific Information Security Policies
Generic Information
Security Standards,
Frameworks and
Models
Information Security Procedures
Information Security Requirements
and Documentation
Source: COBIT 5 for Information Security, Figure 10
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
- 6. APO03 Manage
Enterprise
Architecture
EDM02 Ensure
Benefits Delivery
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
BAI09 Manage
Assets
BAI02 Manage
Requirements
Definition
.
Source: COBIT 5, figure 16
DSS01 Manage
Operations
DSS02 Manage
Service Requests
and Incidents
Deliver, Service and Support
BAI08 Manage
Knowledge
BAI01 Manage
Programmes and
Projects
DSS04 Manage
Continuity
BAI04 Manage
Availability
and Capacity
APO11 Manage
Quality
APO04 Manage
Innovation
EDM03 Ensure
Risk Optimisation
DSS05 Manage
Security
Services
BAI05 Manage
Organisational
Change
Enablement
APO12 Manage
Risk
APO05 Manage
Portfolio
DSS06 Manage
Business
Process Controls
BAI06 Manage
Changes
APO13 Manage
Security
APO06 Manage
Budget and Costs
EDM04 Ensure
Resource
Optimisation
Processes for Management of Enterprise IT
DSS03 Manage
Problems
BAI10 Manage
Configuration
BAI03 Manage
Solutions
Identification
and Build
APO09 Manage
Service
Agreements
APO08 Manage
Relationships
Build, Acquire and Implement
APO10 Manage
Suppliers
APO02 Manage
Strategy
APO01 Manage
the IT Management
Framework
Align, Plan and Organise
EDM01 Ensure
Governance
Framework Setting
and Maintenance
Evaluate, Direct and Monitor
Processes for Governance of Enterprise IT
COBIT 5 Process Reference Model
BAI07 Manage
Change
Acceptance and
Transitioning
APO07 Manage
Human Resources
EDM05 Ensure
Stakeholder
Transparency
MEA03 Monitor,
Evaluate and Assess
Compliance With
External Requirements
MEA02 Monitor,
Evaluate and Assess
the System of Internal
Control
MEA01 Monitor,
Evaluate and Assess
Performance and
Conformance
Monitor, Evaluate
and Assess
for Information
Security
- 7. for Information
Security
COBIT 5 Enterprise Enablers
4. Culture, Ethics
and Behaviour
3. Organisational
Structures
2. Processes
1. Principles, Policies and Frameworks
6. Services,
Infrastructure
and Applications
5. Information
7. People,
Skills and
Competencies
Resources
Source: COBIT 5, figure 12
Enabler Performance
Management
Enabler Dimension
COBIT 5 Enablers: Generic
Stakeholders
Goals
Life Cycle
Good Practices
• Internal
Stakeholders
• External
Stakeholders
• Intrinsic Quality
• Contextual Quality
(Relevance,
Effectiveness)
• Accessibility and
Security
• Plan
• Design
• Build/Acquire/
Create/Implement
• Use/Operate
• Evaluate/Monitor
• Update/Dispose
• Practices
• Work Products
(Inputs/Outputs)
Are Stakeholders
Needs Addressed?
Are Enabler
Goals Achieved?
Is Life Cycle
Managed?
Are Good Practices
Applied?
Metrics for Application of Practice
(Lead Indicators)
Metrics for Achievement of Goals
(Lag Indicators)
Source: COBIT 5, figure 13
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
- 8. for Information
Security
p
do
we
t
re ?
(middle ring)
fi n
e?
to b
ed
ge
th e
ap
m
Co o
De
• Change enablement
ant
te
n
(outer ring)
ew
cu
ow
I d e n tif y r o l e
pla ye rs
oa
e
s
er
ta
B u il d
i m pro
ve m e nts
m
ut u ni
co c a
m e te
fi
rg n e
ta e t
te
e
en n t
ts
• Programme management
• Continual improvement life cycle
(inner ring)
dm
Operate
and
measur
e
Embed n
approach ew
es
Realise ben
efits
le m
I m p o ve m
r
imp
at
er
O p d us
an
E xe
5H
e
De
re we now?
here a
Recog
need nise
act to
ementation
impl
rm team
Fo
r
nito
Mo and
ate
alu
ev
2W
Establ
is
to ch h des
ang ire
e
n
stai
Su
la
Initiat
e pr
ogr
am
me
ow
e
ctiv
ffe
e
re th
ed
rive
rs?
ss
Asseent
curr te
sta
6 Did we get the
ow
1 What a
going?
entum
mom
the
p
kee
we
viewness
do
Re
ms and
probleities
ine
un
Def opport
re?
7H
The Seven Phases of the Implementation Life Cycle
P la n p ro g ra m m e
3
4 W hat n eeds to be d one?
Wh
er
Source: COBIT 5, figure 17 and COBIT 5 Implementation, figure 6
Summary of the COBIT 5 Process Capability Model
Generic Process Capability Attributes
Performance
Attribute (PA) 1.1
Process
Performance
Incomplete
Process
Performed
Process
0
PA 2.1
Performance
Management
PA 2.2
Work
Product
Management
Managed
Process
1
PA 3.1
Process
Definition
PA 3.2
PA 4.1
Process
Process
Deployment Management
Established
Process
2
Predictable
Process
3
COBIT 5 Process Assessment
Model—Performance Indicators
PA 4.2
Process
Control
PA 5.1
Process
Innovation
PA 5.2
Process
Optimisation
Optimising
Process
4
COBIT 5 Process Assessment
Model–Capability Indicators
Process Outcomes
Base Practices
(Management/
Governance
Practices)
Work
Products
(Inputs/
Outputs)
Generic Resources
Generic Practices
Source: COBIT 5, figure 19
©2013 ISACA. A
l l
r i g h t s
r e s e r v e d
.
Generic Work Products
5