MESH WIFI.pdf
- 1. MESH WI-FI NETWORK What is a Mesh Wi-Fi Network and how does it work? How does is differ from a regular Wi-Fi network? BONEY MAUNDU SLIM BZ TECHSYSTEMS
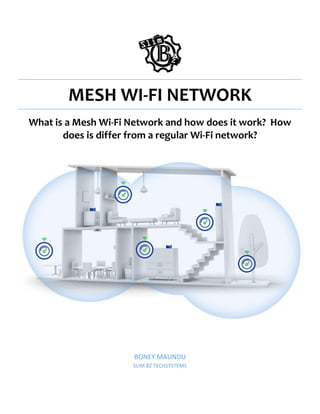
- 2. In a typical large home, office, or business setup, there are Wi-Fi dead spots or areas with significantly weakened Wi-Fi signals, which could be caused by a myriad of things, including physical obstructions like walls, doors, and floors that come between the internet router and end devices. One other cause of weakened signals and Wi-Fi dead spots is simply the distance between the router and end devices, particularly in a large home or building. A regular Wi-Fi router or access point can only transmit signals up to a limited distance, so devices beyond the reach of the Wi-Fi signal become underserved. A mesh Wi-Fi system, also known as a whole-home Wi-Fi system, uses a series of nodes or access points that connect to each other and expand the reach of a wireless signal. It’s flexible and easily scalable, which enables a customizable method of expanding Wi-Fi reach without the use of range extenders, which usually degrade network performance. The network infrastructure is decentralized and simplified, as one node or access point only needs to transmit as far as the next node or access point closest to it. A wireless mesh network may or may not be connected to the internet, for example, in the case of a wireless alarm system in a large home or building. Wireless mesh networks can be used in applications where end-user nodes are too far apart to share a direct wireless connection to the central router. Apart from the home, office, or business, other applications might include temporary locations like events or construction sites. Mesh systems are usually paired with guided setup apps that enable analysis, setup, management, and placement of nodes throughout the home or building. How does a mesh Wi-Fi network work? A mesh Wi-Fi system consists of a main router (or modem) that connects directly to a series of modules or nodes placed around a home to achieve full Wi-Fi coverage, creating a single wireless network that shares the same SSID and credentials. In a modular configuration, one node or access point connects to an internet router (or modem). The node then connects to an additional node, which can also connect to another node down the line in a daisy chain configuration, providing a seamless, self-perpetuating network.
- 3. In a mesh network, all the components of the network, i.e., the satellite access points and router, work together to create a single seamless roaming network. It differs from range extenders, which work independently and require a user to manually log in to different range extenders placed all over the house or building. For the mesh network to work, two or more identical mesh routers are needed to create a mesh of routers, with one router acting as the hub or gateway device through which the internet signal comes into the building. The other routers placed within range of the hub or each other rebroadcast the signal further, creating a mesh of devices. To extend the network, more routers or access points are added that connect to the nearest existing nodes and self-calibrate to accommodate new devices. Mesh networks find the most optimal connections between mesh routers and end-point devices to route traffic. When one mesh router goes down or becomes too congested, the mesh wireless network reroutes traffic around the unavailable or ineffective nodes in a bid to maintain consistent network performance. In the case of a range extender, a user has to switch to a different network every time they stray beyond the reach of the original Wi-Fi router's signal and, in the process, experience diminished network performance as range extenders cut network performance significantly and create a bottleneck effect. Mesh Router vs. Regular Router In a configuration with a regular router, Wi-Fi signals are broadcast from a single router with limited reach, whereas in a mesh network, mesh routers strategically placed around the home or building within reach of at least one other mesh router transmit signals from multiple units. With a regular router, the Wi-Fi signal being transmitted from a central point weakens and degrades as it travels further from the router. The devices further from the router or those obstructed by its Wi-Fi signal will experience limited speeds and bandwidth as they can only connect to the central router. This may necessitate the addition of wireless range extenders to take care of the Wi-Fi dead zones. On the other hand, with mesh routers, a mesh (or web) spans the entire building, and end-point devices do not have to connect to the central hub but to the closest available mesh router, which might be right next to them. The mesh routers or nodes connect to each other optimally, routing traffic between themselves and end-point devices, allowing data to hop from one router to the other until it reaches the gateway router. The nodes are programmed to utilize adaptive routing algorithms to determine the most optimal routes between themselves for effective and consistent transmission and network performance.
- 4. Mesh vs. range extenders There is a slight similarity between how mesh routers and wireless range extenders work. In a small home with acceptable Wi-Fi coverage and one or two small Wi-Fi dead spots, or where weak Wi-Fi coverage is not a burning issue, a range extender might suffice. The downside of range extenders is that once they connect to the internet router or access point, they rebroadcast the significantly degraded signal with a new network SSID, thereby creating an entirely new network. While range extenders can still connect to each other in a daisy chain, that would exacerbate network degradation even to the point of making them an actual bottleneck. A mesh network, on the other hand, retains both the network name and credentials in addition to maintaining the internet router’s speeds and bandwidth, thereby ensuring the network is not degraded. Mesh routers in a mesh network are designed to communicate with each other and have the same interface, firmware, and settings. Advantages of mesh networks They’re easily scalable, as nodes can be wirelessly added to the network. They’re reliable since each node can be connected to several other nodes or access points, ensuring that if one node drops, data can be rerouted through the other connected nodes. Unlike wireless range extenders, they can expand W-Fi range across the home or building without affecting network performance through reduced speeds and bandwidth. Only one node needs to connect to the internet, and the rest of the nodes can connect to it and route traffic between each other and end-user devices. Most mesh network applications and platforms come loaded with features that help in network management and optimization, including parental control, guest access, ad-blocking, remote management, and others. Downsides of mesh networks A mesh network is decentralized, and this decentralization can make routing and network management, control, troubleshooting, and monitoring more complex than a centralized network. In a home application, more mesh routers may be costlier than a regular Wi-Fi router network configuration. Slow networks might have more latency as data will often need to hop between several nodes as it travels back and forth between the end-user devices and the main internet source. Initial setup may be complex, as the ideal placement of nodes might require careful planning and consideration for the network to work optimally. The network topology of a wireless mesh network can either be partial or full mesh. A full mesh network is one where every node connects to every other node, while in partial mesh topologies, a node communicates only with the nearest node. The mesh network can also be a combination of wirelessly connected nodes and wired nodes.
